DevSecOps with Azure and GitHub
In the fast-paced world of software development, security often takes a backseat to speed and efficiency. However, with the rise of cyber threats, integrating security into every phase of the development process has become imperative. This is where DevSecOps comes in, blending development, security, and operations into a unified framework. Let’s explore how Azure and GitHub can be leveraged to create a robust DevSecOps environment.

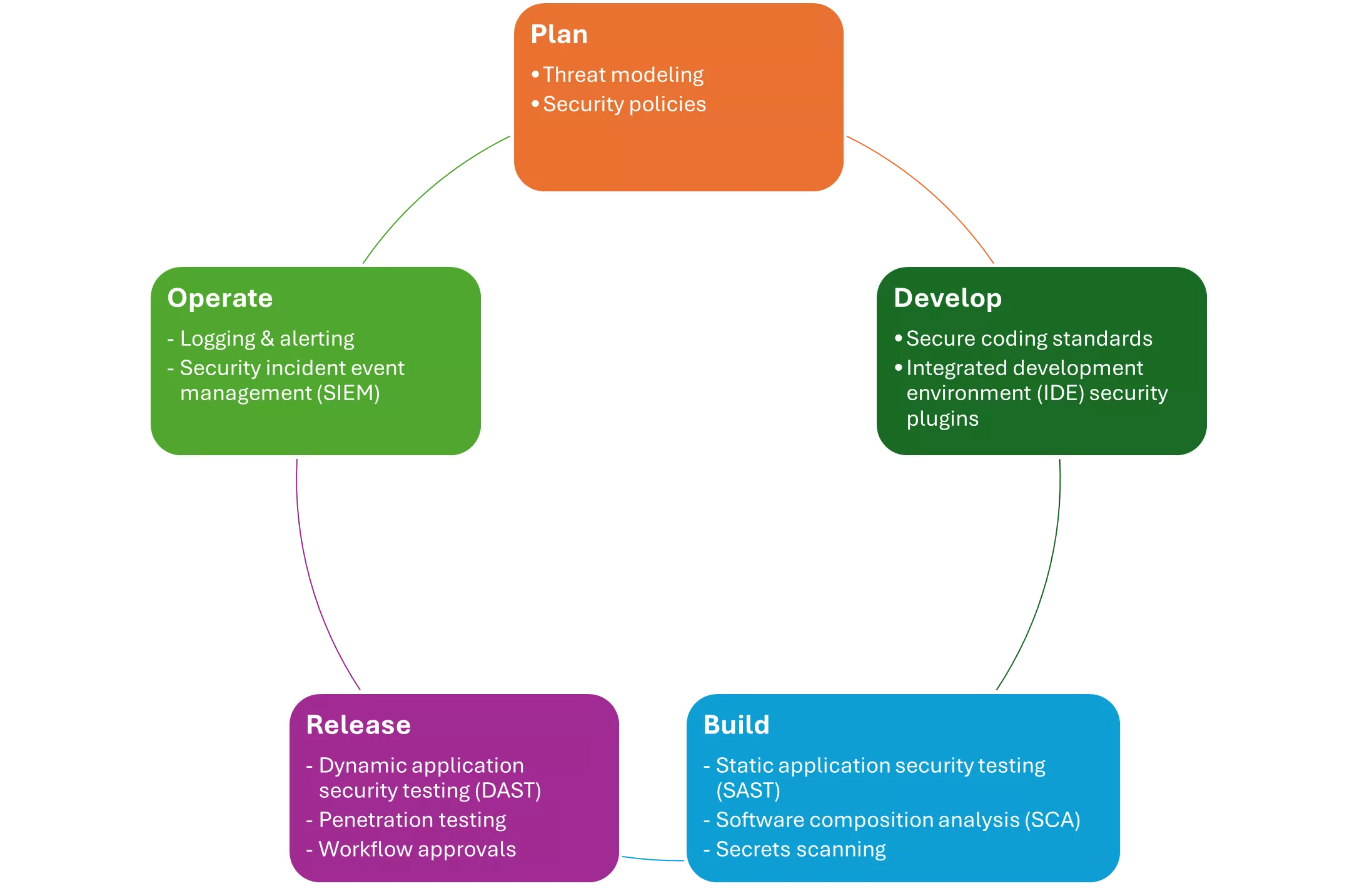
DevSecOps lifecycle stages
Security controls are implemented in each phase of the software development lifecycle (SDLC). This implementation is a key piece of a DevSecOps strategy and of the shift-left approach.
- Plan phase – This phase involves collaboration between security, development, and operations teams.
- Develop phase – This process begins before code is even committed into a repository and deployed via a pipeline. Adopting secure coding best practices and using IDE tools and plugins will enhance overall security of the SDLC.
- Build phase – Developers work with the site reliability engineers and security teams to integrate automated scans of their application source within their CI build pipeline.
- Deploy phase – Developers, application operators, and cluster operators work together to establish the right security controls.
- Operate phase – Operation monitoring and security monitoring tasks are performed to proactively monitor, analyze, and alert on potential security incidents.
Azure: A Cloud Platform with Security
Microsoft Azure provides a comprehensive set of tools that support the DevSecOps approach. Azure DevOps, a suite of services covering planning, collaboration, testing, and deployment, is at the heart of this ecosystem. It offers:
- Azure Repos: Secure Git repositories for source control.
- Azure Pipelines: CI/CD pipelines that integrate automated security testing.
- Azure Artifacts: Component management with security scanning for packages.
- Azure Security Center: Unified security management and advanced threat protection.
GitHub: Platform for version control, collaboration, and security
GitHub is not just a repository hosting service; it’s a platform where code collaboration and security converge with features like:
- GitHub Actions: Automate workflows and integrate security checks within the CI/CD pipeline.
- GitHub Security Alerts: Get notified about vulnerabilities in your dependencies.
- GitHub Advanced Security: Access advanced code scanning and secret scanning capabilities.
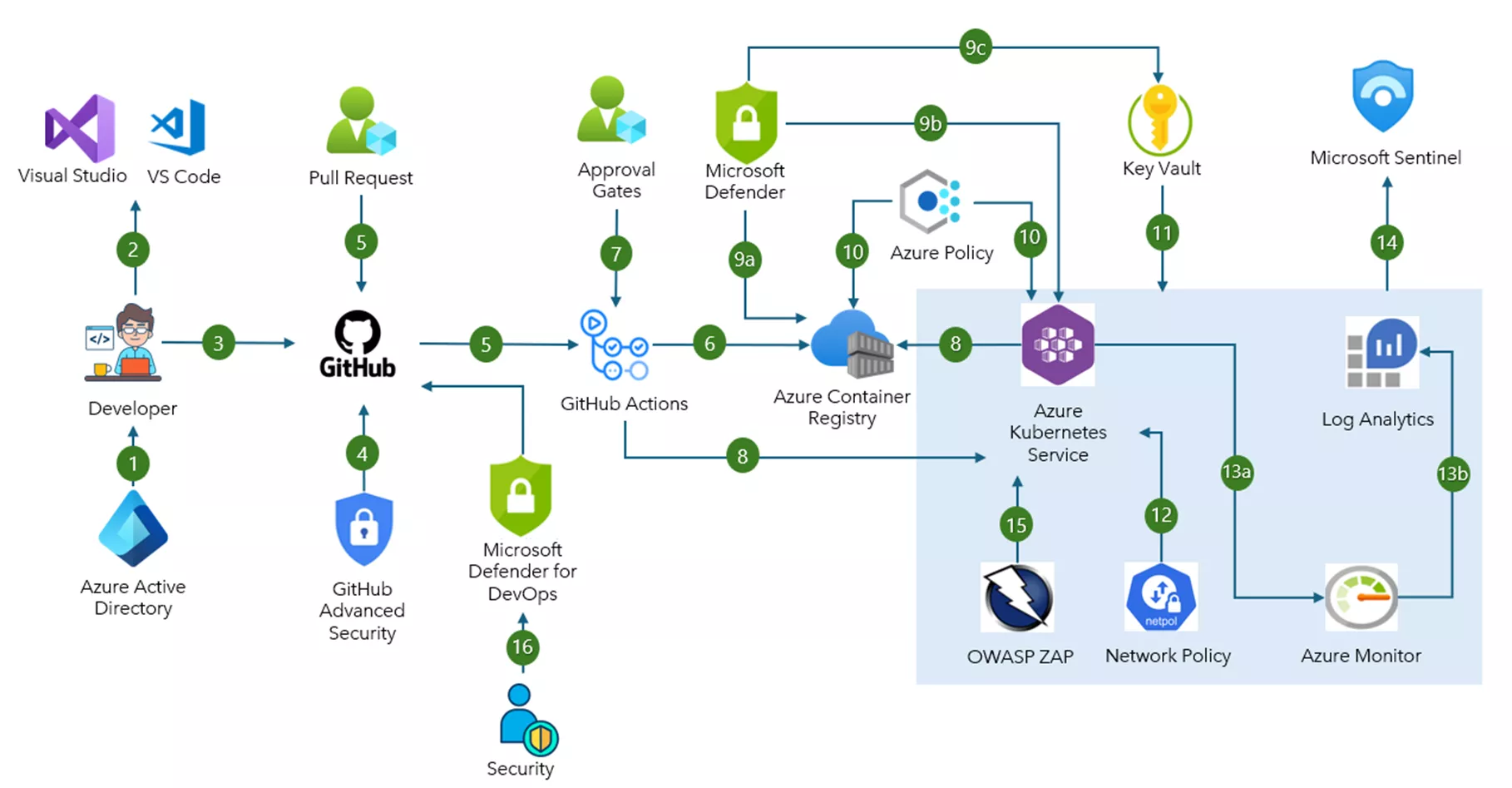
Reference – Microsoft official website
Image – Implementation of security in existing DevOps pipeline
- Azure Active Directory (Microsoft Entra ID) is configured as the identity provider for GitHub. Configure multi-factor authentication (MFA) to help provide extra authentication security.
- Developers use Visual Studio Code or Visual Studio with security extensions enabled to proactively analyse their code for security vulnerabilities.
- Developers commit application code to a corporate owned and governed GitHub Enterprise repository.
- GitHub Enterprise integrates automatic security and dependency scanning through GitHub Advanced Security.
- Pull requests trigger continuous integration (CI) builds and automated testing via GitHub Actions.
- The CI build workflow via GitHub Actions generates a Docker container image that is stored to Azure Container Registry.
- You can introduce manual approvals for deployments to specific environments, like production, as part of the continuous delivery (CD) workflow in GitHub Actions.
- GitHub Actions enable CD to AKS. Use GitHub Advanced Security to detect secrets, credentials, and other sensitive information in your application source and configuration files.
- Microsoft Defender is used to scan Azure Container Registry, AKS cluster, and Azure Key Vault for security vulnerabilities.
- Microsoft Defender for Containers scans the container image for known security vulnerabilities upon uploading it to Container Registry.
- You can also use Defender for Containers to perform scans of your AKS environment and provides run-time threat protection for your AKS clusters.
- Microsoft Defender for Key Vault detects harmful and unusual, suspicious attempts to access key vault accounts.
- Azure Policy can be applied to Container Registry and Azure Kubernetes Service (AKS) for policy compliance and enforcement. Common security policies for Container Registry and AKS are built in for quick enablement.
- Azure Key Vault is used to securely inject secrets and credentials into an application at runtime, separating sensitive information from developers.
- The AKS network policy engine is configured to help secure traffic between application pods by using Kubernetes network policies.
- Continuous monitoring of the AKS cluster can be set up by using Azure Monitor and Container insights to ingest performance metrics and analyse application and security logs.
- Container insights retrieve performance metrics and application and cluster logs.
- Diagnostic and application logs are pulled into an Azure Log Analytics workspace to run log queries.
- Microsoft Sentinel, which is a security information and event management (SIEM) solution, can be used to ingest and further analyse the AKS cluster logs for any security threats based on defined patterns and rules.
- Open-Source tools such as Zed Attack Proxy (ZAP) can be used to do penetration testing for web applications and services.
- Defender for DevOps, a service available in Defender for Cloud, empowers security teams to manage DevOps security across multi-pipeline environments including GitHub and Azure DevOps.
Best Practices for DevSecOps Success
- Collaboration is Key: Encourage open communication between developers, security teams, and operations.
- Continuous Learning: Stay updated with the latest security trends and tools.
- Automate Everything: The more you automate, the less room there is for human error.
- Feedback Loops: Implement monitoring and alerting to quickly respond to security incidents.
Conclusion
By integrating Azure and GitHub into your DevSecOps strategy, you can create a secure, agile, and efficient development pipeline. Remember, security is a journey, not a destination. It requires continuous effort, adaptation, and commitment from the entire team.
DevSecOps can be effectively implemented with Azure and GitHub to enhance the security and quality of software development projects.
Top-tier DevSecOps methodologies enhance security and streamline development operations. We can help you with end-to-end software development by incorporating DevSecOps practices. Decos offers comprehensive services to help you seamlessly integrate security into every phase of your development lifecycle.
Contact us today to learn more about how we can support your journey towards a secure and efficient DevSecOps environment with Azure and GitHub.

This blog is written by Yuvraj Sonale, Senior DevOps Engineer at Decos. He has been working on projects and successfully helping clients to reduce downtime and enhancing the overall efficiency of IT operations.
Decos is a cutting-edge technology services partner ready to meet your diverse needs across various industries, including the medical domain. If you have a question on one of our projects or would like advice on your project or a POC, contact Devesh Agarwal. We’d love to get in touch with you!
Discover more
Critical Role of Medical Device Labelling: Ensuring Safety, Compliance, and Patient Well-being

Exploring the Capabilities of OpenAI API